The Internet of Things (IoT) is a connected network of objects and people that collaborate to achieve specific goals. It is enabled by sensors, actuators, communication devices and computers that exchange and process myriad types of data and is able to interface with users in a most intuitive way. Sensors may register motion, vibration, light, pressure, sound, temperature, chemical concentrations, or electrical data that is collected, transmitted and analyzed for many different purposes. Projections say that about 5 billion objects are already connected to the Internet around the world, up 30 percent in just one year. Explosive growth is expected, as much as 500 percent, to 25 billion objects by 2020.[1] These objects, many of which are ‘smarter’ versions of commonplace items, will have impacts felt in our homes, businesses, social lives, and used in many ‘behind the scenes’ functions, of which we may not be aware.
Depending on individual viewpoints, the IoT may be an exciting development, making us healthier, safer, or more efficient and productive, more profitable, more entertained, or more fulfilled experientially, or it may be the beginning of a frightening new world where constant surveillance removes all traces of privacy. The reality is likely to be something in between. However, it is easy to understand some fears—some of the defining qualities of living beings: the ability to sense surroundings, process information and act on it, are exactly the things that machines and ordinary nonliving objects are being enabled to do through the IoT.[2]
Internet of Things in the home
Energy savings—One benefit IoT promises is improved energy efficiency. Products for controlling energy use in homes were among the first Internet connected devices for consumers (Figure 1). Controls for thermostats, lighting, window blinds, and hot water heaters can be remotely controlled and can display real time energy use to an in-home dashboard, a computer or smartphone app. Smart thermostats with occupancy sensors can learn daily routines and automatically set the home temperature higher or lower to save energy when the occupants are not home.

Figure 1. Various in-home energy monitors. [Click for full size image.] Credit: Energy.gov
Home energy management services can also save money by reducing power consumption (with homeowner permission) for short periods during peak energy demand periods. If a large number of consumers participate, utility companies can avoid running their most expensive power plants and return some of the savings to participating customers. This type of scheme has worked for commercial and industrial customers in the past and is being extended to residential customers in limited markets.[3] Residential customers must have smart meters, and utilities must have a significant cost differential between the minimum and maximum power demand that they must meet (termed base and peak loads) for this arrangement to be feasible.
Here is a sampling of IoT devices for the home:
- Doorbells can send alerts to a smartphone when a visitor is present, allowing you to both see and speak with them remotely. These can be activated by a motion sensor as well as the actual push button and can store a video of the event.
- A new mattress cover claims to improve sleep by monitoring breathing, heart rate and movements, to learn an optimal temperature and automatically adjust the room’s thermostat. It also will wake the sleeper during a light phase of sleep, to reduce morning grogginess.[4]
- An internet-connected refrigerator can multi-task with a built-in touch screen, TV, VCR, DVD, microphone, speaker, and camera.[5] However, its main function is to help keep up with what’s in the refrigerator and to lessen spoilage by warning about pending expiration dates. Foods with packaging containing a Radio-frequency Identification Devices (RFID) are automatically added to an inventory by date and moved to a shopping list when they are used. Other foods that lack the RFID must be manually added to the inventory. A shopping list can be generated when desired and transmitted to the grocery store to be picked up or perhaps delivered.[6]
- A posture sensing fabric on a chair can remind its occupant to sit up straight and a fork will alert its user to slow down while eating.[7]
- Interactive toys are being developed that can engage a child in conversations, asking questions to learn the child’s interests and abilities, then proposing appropriate stories and games.[8]
Health applications
Wearable activity monitors have mushroomed in popularity, counting the steps, calories burned, heartrate and other measures of the wearer’s activity. These are also being incorporated into clothing, and can be effective tools to encourage active lifestyles. Beyond fitness, monitors for various medical conditions are becoming available. Devices for epileptic seizures can detect changes in the wearer’s respiration rate and electrical activity in the skin, then wirelessly alert caregivers of a possible problem.[9] For the millions of diabetics in the U.S., several types of sensors are being used to frequently measure blood sugar levels. The readings are transmitted to a small receiver, trends are predicted based on previous readings and the results shared with family members or a doctor.[10] Fall detectors, blood pressure monitors and devices that report whether medications have been taken are potentially lifesaving for elderly persons. Wearable cancer detectors and cameras contained in pills may help doctors diagnose diseases earlier, and wearable devices for children can monitor health indicators and alert parents if set thresholds are crossed (Figure 2).
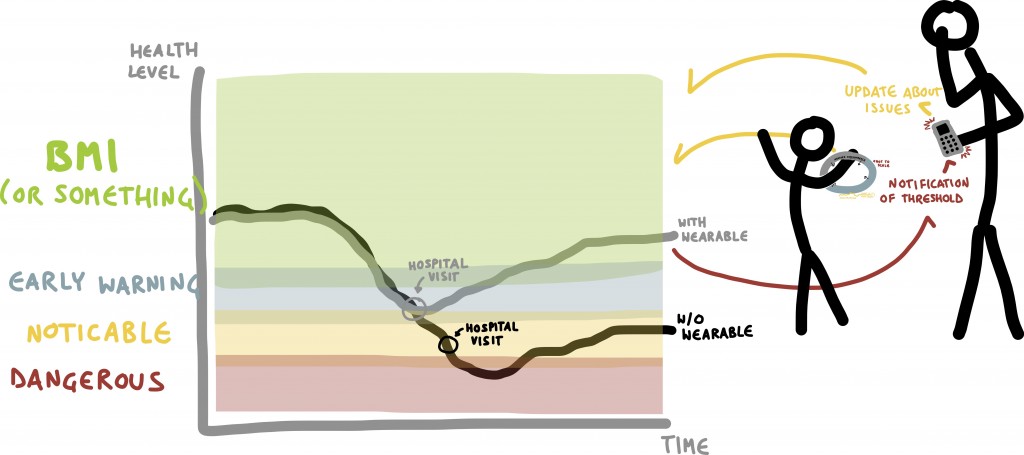
Figure 2. Wearable devices can help parents monitor a child’s health. [Click for full size image.] Credit: By Willowb100 (Own work)
Internet of Things at work
New products are intended to make workers safer and more productive. The Bureau of Labor Statistics reported in 2013 that musculoskeletal injuries made up one third of all injury and illness on the job.[11] One two-piece device, worn on the back and the wrist, is designed to prevent back injury by monitoring which muscles are being used while lifting. It can be worn by anyone concerned with preventing back injury, particularly warehouse, construction, factory or health care workers, and provides immediate feedback to the wearer as to whether a lift was done safely. If not, the person’s lifting posture can be modified.[12] For those sitting most of the day in office jobs, chairs with pressure sensors pay attention to the worker’s posture and can prod him or her to sit up straight to prevent back problems.
Worker’s performance can also be tracked on the job with an app on a smart watch, phone or computer. Colleagues are intended to interact through the app, providing competition and encouragement in a form of goal oriented social media for the office.[13]
Internet of Things in the community
Many internet-connected devices are not consumer products, and we may not be aware of them. Nevertheless, they are integral parts of current and future technology.
Infrastructure—Critical infrastructure such as electric power generation plants and transmission grid, water and wastewater treatment plants, pipelines, and dams are increasingly using sensors to collect operational data, monitor processes and provide alerts for abnormal circumstances. In some cases, computers diagnose problems and take corrective actions. For example, a smart electric grid is capable of detecting faults or irregularities in the system and is able to very quickly re-route electric power to avoid large-scale outages.
Transportation—Some new cars are already featuring smart safety devices, including cruise control that maintains a safe distance between cars on highways, sensors to prevent the car from backing up if an object is behind it and automatic brakes. Event data recorders (EDRs) keep a record of the vehicle’s speed over time that may be retrieved if an accident occurs. Self-driving cars are already being tested on the road, and although they have a relatively high accident rate, the manufacturer says the self-driving cars are not to blame.[14] On the highway itself, traffic monitors can notify officers if traffic lights malfunction. Location tracking with GPS devices let trucking companies know where their drivers are and how fast they are driving. IoT anti-theft systems can automatically be turned on if a vehicle is stolen and report the location through an app on the owner’s smart phone.[15]
Security systems—Video surveillance cameras connected to computers are now capable of learning normal patterns of human behavior and can set off alerts when someone behaves in a different way. A computer programmer does not have to imagine every possible condition in advance; instead, the program responds to circumstances out of the ordinary and notifies an appropriate individual.[16]
Personal items—Internet connected watches, glasses and fitness devices are being produced by a growing number of companies. Many apps available on smart phones are being designed for use on a wearable item.
Challenges for the Internet of Things
Consumer acceptance—Consumers must be convinced that new devices are beneficial and sufficiently secure before they can gain wide acceptance. It won’t happen if consumers can’t afford them or don’t see their benefits. Some consumers worry that information from smart utility meters or other objects transmitting within their homes could alert would-be intruders to times when the home is unoccupied. The privacy lost by almost ubiquitous cameras and location tracking by many devices is another concern for some consumers.
Technical issues—With new technology, there are technical issues to overcome. Smaller, more powerful computer chips have enabled smart features to be built into many objects. Sensors powered with solar energy or energy from small vibrations as a person or object moves can lessen the need for batteries and power plugs. In addition, open platforms are needed if devices are to interface and share data with each other. Common communication protocols allow hardware, software and different systems to communicate.[17]
Perhaps one of the most challenging aspects of IoT is how to program it. For example, third party applications that can use devices in the home may be developed and accessed through an app store. A Baseball League app on a smart phone, for instance, might recognize that the home has a Digital Video Recorder (DVR) and offer to record a game as a service to the app user, rather than requiring the user to open the app, find the game schedule, then move to the living room to manually program the DVR. This type of programming is different from the current functionality of phones and DVRs. Both smartphones and DVRs are connected to the internet today, yet they are not enabled as an IoT. When they are part of an IoT, it will be possible to develop third party apps that harness their collective functionality in creative ways of interest to the user.
Data security—We generate data every time we look up information on the internet, check social media, make phone calls or make financial transactions with credit cards. It is easy and inexpensive for companies to collect and store our data, and they do, often for targeted advertising themselves or for sale to other companies who see a financial gain from information they can filter or infer from the data. Maintaining privacy of personal data is not an easy task. Many businesses have been caught with insufficient security, and hackers have been successful in stealing millions of personal records. Data encryption offers some protection, but constant improvements are needed.
More than an inconvenience, hacking of implantable medical devices could pose a risk to patients from a deliberate cyber-attack or an incidental virus spread through the internet. Devices linked through hospital Wi-Fi systems with two way communication could have settings changed—perhaps the rate of a pacemaker causing unintended consequences for the wearer. To date, there have not been reported instances of outsiders either intentionally or unintentionally targeting medical devices. However, the Department of Homeland Security, the Food and Drug Administration, manufacturers and others, are working to identify any security flaws in equipment and reduce vulnerability to prevent intrusions and protect patient privacy.[18], [19]
Data collection and management vs. privacy—There are many questions to be answered about data collection and privacy including: Who may collect and store personal data, and for what purposes? How long can it be kept? Does an individual have control over what is collected and how it is used? If a choice is given, should it be on an opt-out or an opt-in basis? There are many variables to consider when evaluating the sensitivity of citizens to the use of data collected about them; some are objective variables for which rules can be clearly defined, while others are subjective variables that are open to individual interpretation (Figure 3). As more data is collected there is a need for greater transparency and better understanding of the context surrounding our personal data. For example, contrary to what many believe, currently in the United States, consumers do not own the legal rights to their own information, including medical records.[20]
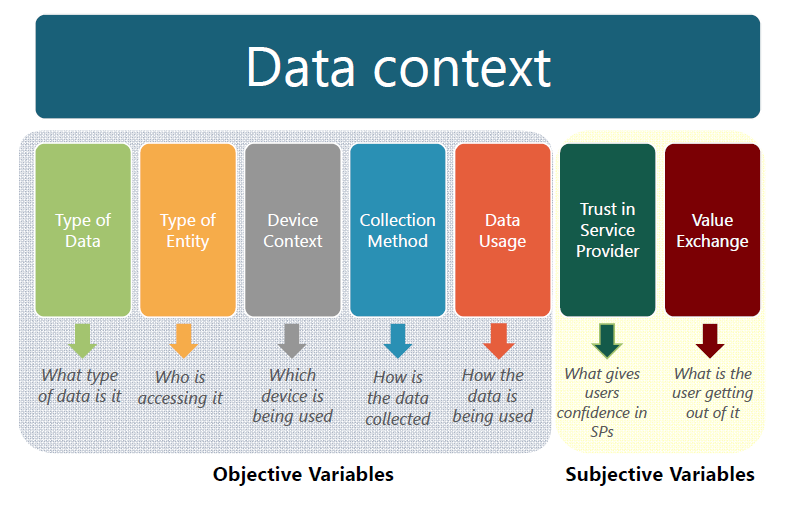
Figure 3. Variables surrounding data collection and use. [Click for full size image.] Credit: Federal Trade Commission, Internet of Things Workshop
The most commonly accepted standards governing management of consumer data are the Fair Information Practices, used as the basis for many state laws as well as by international organizations and countries. They include:
- Data collection must be transparent—consumers must be told what is being collected and its purpose. Only the minimum data genuinely needed should be collected.
- Individuals have a choice whether to allow information to be used beyond its initial purpose.
- Data must be accurate; consumers need a process to review and correct inaccurate information
- Organizations must maintain security to prevent the loss, modification or destruction of data and be accountable for any lapses.[21]
The Federal Trade Commission (FTC) issued a report in January 2015 warning of the dangers to privacy and security from the IoT and outlining specific steps for businesses to minimize risks. It cautioned that consumer trust is essential to the full success of the IoT. The Commission can use several existing laws, such as the FTC Act, The Fair Credit Reporting Act and the Children’s Online Privacy Protection Act to enforce some privacy limits, but it believes that additional legislation is needed to mandate data security and notifications of security breaches to the public.[22]
Effects on society: convenience or nightmare?—Even if the IoT clears all its technical and privacy hurdles, will it be dependable? Will citizens in their smart homes or in the smart city get to rely on IoT and its services to the point that they expect these service to be continuously available? Some components in the IoT are not necessarily highly reliable, e.g. sensor hardware is fragile with limited lifetime energy. Frustration with malfunctions or failures could make some users reject them. Before massive investments are made, users’ expectations should be carefully managed or the return on society’s investment could be diminished.
For all the advantages offered by the IoT, could there be unintended consequences? For instance, video cameras that predict ‘normal behavior’ may provide effective security, but some worry about the risk of society too rigidly defining what is normal and the potential stifling effect of constant surveillance on creativity and individuality.[23] The practice of companies defining personal profiles to select music and advertising that may interest us poses another question. Have we (perhaps unthinkingly) limited our choices by giving up some control over what we hear and see? More importantly, will a commercial app choose the news and information that we see based on our ‘interests’, making us less likely to be exposed to differing opinions or develop new interests? If it’s not necessary to learn to read a map or drive a car, will we lose something? It is certain that the IoT is bringing changes to society, but we have choices in how we use these new devices. We also have an individual and collective challenge to monitor and moderate their effects on privacy and society.
Resources
Postscapes and Harbor Research:
Infographic: What exactly is the “Internet of Things”?, March 2014.
National Institute for Standards and Technology:
Fair Information Practice Principles
National Strategy for Trusted Identities in Cyberspace, NSTIC Guiding Principles, Benefits of NSTIC and FAQ.
U.S. Federal Trade Commission:
News Release, January 27, 2015, FTC Staff Report: Internet of Things, Privacy and Security in a Connected World.
How to Keep Your Personal Information Secure, July 2012.
Computer Security, accessed June 15, 2015.
Kids’ Online Safety, accessed June 15, 2015.
World Economic Forum (WEF):
WEF and the Boston Consulting Group, Unlocking the Value of Personal Data: From Collection to Usage, February 28, 2013.
Technology Pioneers 2015, 24 start-up companies developing new technology, many of which are connected to the IoT.
Acknowledgements
Author: Lynn Jarretta
Reviewers: Sumi Helalb ,Charles Kilbertc
a Program for Resource Efficient Communities (PREC), University of Florida
b Computer and Information Science and Engineering, Mobile & Pervasive Computing Laboratory, University of Florida
c Powell Center for Construction & Environment, University of Florida
First published June 2015.
Footnotes
[1] Gartner, Inc., Press Release, Gartner Says 4.9 Billion Connected “Things” Will Be in Use in 2015, November 2014.
[2] Stifel, Equity Research Industry Analysis, Technology: A White Paper on The Internet of Things “The Dawn of Inanimate Consciousness”, February 2014.
[3] Klint Finley, Wired, The Internet of Anything: The System That Pays You to Use Less Electricity, February 15, 2015.
[4] Ted Burnham, Postscapes, WiFi Mattress Cover: Luna, accessed March 31, 2015.
[5] Mike Hanlon, Gizmag, LG Internet Refrigerator, accessed March 13, 2015.
[6] Ken Black, WiseGeek, What Is a Smart Refrigerator?, March 6, 2015.
[7] Steve Johnson, San Jose Mercury News, Will our smart gadgets become trusted or oppressive companions?, January 17, 2015.
[8] Ted Burnham, Postscapes, Cloud Connected Toys: CognitToys Dino.
[9] Ethan Leng, et al, Rehabilitation Engineering and Assistive Technology Society of North America, Smart Belt: A Low-cost Seizure Detection Device (Rice University), June 13, 2013.
[10] U.S. Food and Drug Administration, Medical Devices, December 12, 2014.
[11] Bureau of Labor Statistics, News Release, USDL-14-2246, December 16, 2014.
[12] Kinetic, Protecting the back bone of our economy, accessed March 5, 2015.
[13] Cade Metz, Wired, A Smartwatch App That Lets Your Boss Track You Constantly, March 4, 2015.
[14] Holman W. Jenkins, Jr., The Wall Street Journal, When Robo-Cars crash, It’s Your Fault, June 9, 2015
[15] Zhigang Liu ,et al, IEEE 978-1-4799-0380, Vehicle Anti-theft Tracking System Based on Internet of Things, January 2013.
[16] Digital Energy Journal, Video surveillance with behavior recognition, April 17, 2014.
[17] Sasa Marinkovic, Information Week, Internet Of Things Demands Open Standards, April 10, 2014,
[18] Homeland Security News Wire, Medical devices, not only medical records, are vulnerable to hackers, January 8, 2015.
[19] Marc Goodman, Slate, Who Does the Autopsy? The criminal implications of implantable medical devices, March 13, 2015
[20] Alison Diana, InformationWeek Healthcare, Who Owns Patient Data, September 2014.
[21] Federal Trade Commission, Privacy Online: Fair Information Practices in the Electronic Marketplace, May 2000.
[22] Federal Trade Commission, Press Release, January 27, 2015.
[23] Steve Johnson, San Jose Mercury News, Will our smart gadgets become trusted or oppressive companions?, 17 January 2015.